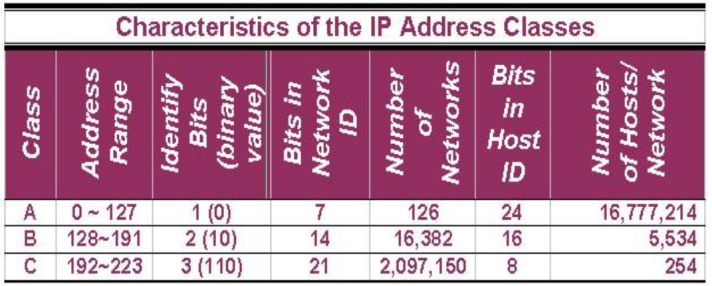
This is the start of computer network post series. In this post I would like to make introduction about computer network. In my undergraduate degree program currently in level two as a subject I am studying computer network.
First what is computer network? We can consider computer network as” Computer network is a collection of computers & devices connected by communication channels that facilitate communication among the users and allow users to share resources with other users. ”
But remember” A single computer system with its peripherals such as printers, scanners etc. is not considered as a network”.
There are lot of advantages in computer networks. Some of them are,
- Accessing databases, transferring, processing and retrieval of data can be done on-line
- Online credit card checking, e-commerce and Electronic Fund Transfer are possible
- Easily administered
- Provides an efficient means of communication such as e-mail, Voice mail, and Video conferencing.
- Users can be easily added or removed.
- Tasks of distributed nature can be processed by distributed computer systems by exchanging data.
- Provides a way to share data, programs, peripherals, computing power and information.
- Provides data security (Comparing to other communication devices).
The major issue regarding to computer network is the security of a computer network is challenged everyday by equipment malfunctions, system failures, computer hackers, virus attacks.
Network types
There are two major types,
- Local Area Network (LAN)
- Wide Area Network (WAN)
Local Area Network (LAN)
A Local Area Network spans a relatively small area. They are usually confined to one building or a group of buildings. Usually privately owned and provides high data rates. The most common type of Local Area Network is called Ethernet.
Wide Area Network (WAN)
A network which covers a very large geographical area such as a country, continent or even the whole world. Provides long distance communication of data or information. Also operating at low speeds (compare to LANs).
There are several types of WANs,
- Metropolitan area network (MAN)
- Public access network (PAN)
- Value added network (VAN)
- Virtual private network (VPN)
Metropolitan area network (MAN)
A network which covers medium geographical area such as a town or a city. Provides high speed connectivity for Internet through DSL / ADSL lines and other services such as cable TV.

Virtual private network (VPN)
Virtual private network is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with access to their organization’s network.
VPN became popular as more employees worked in remote locations. Employees can access the network (Intranet) from remote locations. The Internet is used as the backbone for VPNs. Secured networks. These systems use encryption and other security mechanisms to ensure that only authorized users can access the network and that the data cannot be intercepted.

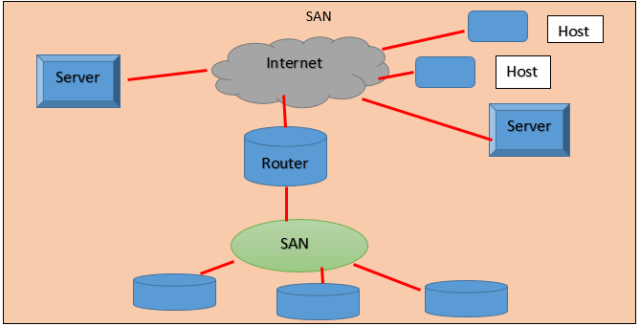
Storage Area Network (SAN)
A Storage Area Network (SAN) is a high-speed special-purpose network (or subnetwork) that interconnects different kinds of data storage devices with associated data servers. Storage is accessed at block level not at file level. In this network simplifies storage administration, high scalability and high performance are some benefits.
Controller Area Network (CAN)
Controller Area Network is a serial bus network of microcontrollers that connects devices, sensors and actuators in a system or sub-system for real-time control applications. It is a dedicated development of the automotive electronics industry.
In next post I will hope to talk more about computer Network.